Risk management, cybersecurity, document management, NIS2, how do these relate?
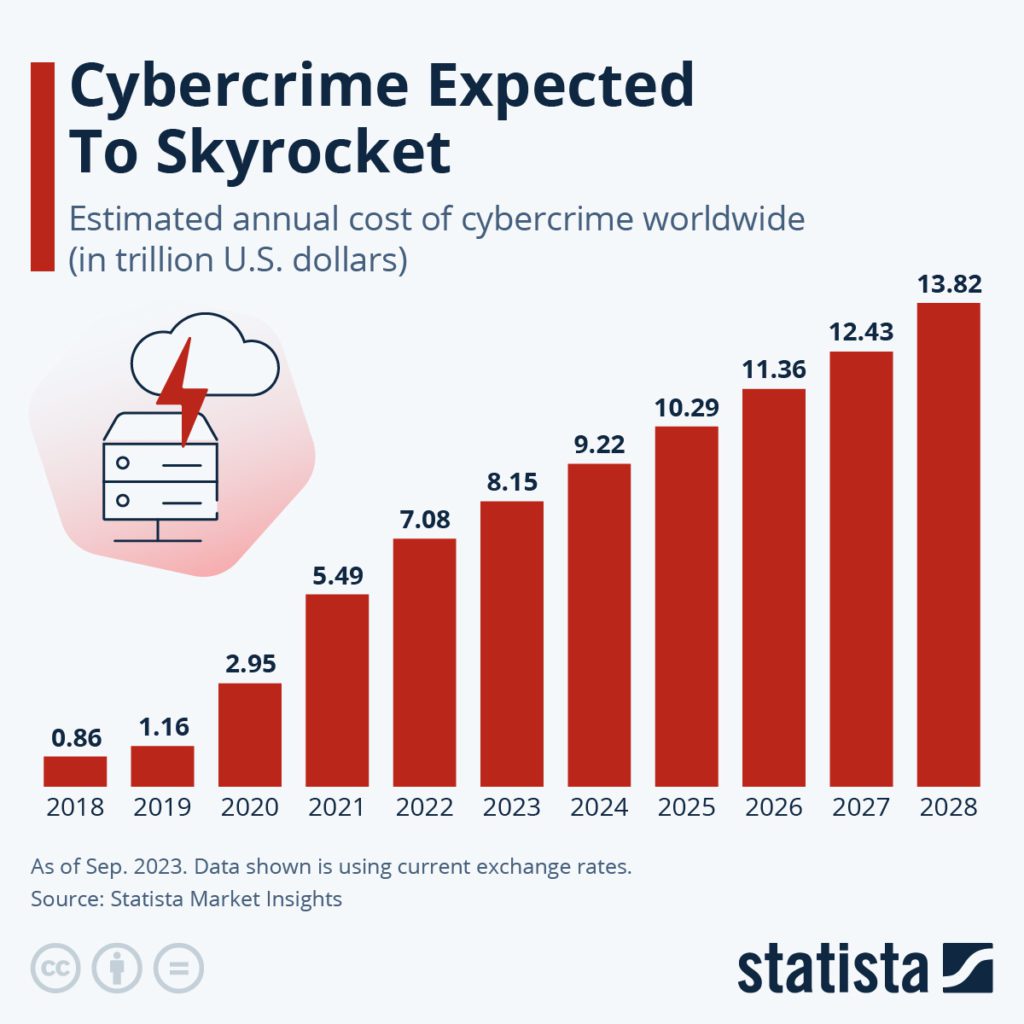
Cybercrime worldwide and in the Netherlands.
The NIS2 (Network and Information Security) directive aims to ensure cybersecurity and the management of cyber incidents to contribute to the safety of the European Union. The costs of cyber incidents are rapidly increasing globally. According to Deloitte, the Netherlands incurs 10 billion euros in damages from cybercrime each year. Research by IT security firm ESET reveals that a cyber incident at an SME in the Netherlands costs an average of around 270,000 euros.
Is the new EU NIS2 directive applicable to your company?
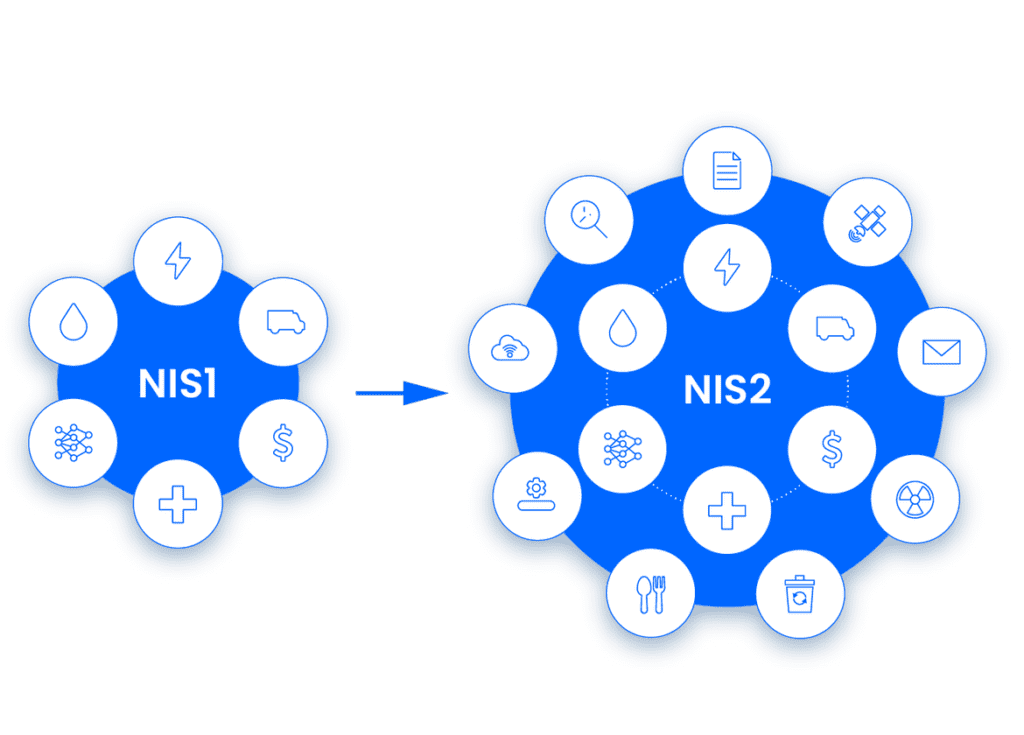
The old NIS1 directive from 2015 applies to about 300 large Dutch organizations in essential sectors such as energy, drinking water, and banks. The NIS2 directive was published in 2022, and member states are required to implement it by October 2024. The Dutch NIS2 law will come into effect in 2025. You can use this handy self-assessment site to check if the NIS2 directive applies to your company. Tip: Click on the question mark to read details per sector.
The new NIS2 applies to more organizations in the Netherlands compared to NIS1. According to CBS, approximately 5000 companies are estimated to become NIS2 obligated. This information comes from a CBS-report from 2020 (Tip: download the table at the bottom of the page). Dutch and Belgian municipalities will likely also become NIS2 obligated.
More companies will be affected by NIS2. Organizations falling under NIS2 will assess their supply chain risks and require suppliers to comply with NIS2.
NIS2 Requirements
NIS2 includes detailed requirements. In essence, we need to address topics typically covered within an information security management system. This includes operational security and emergency planning, usually integrated into a business continuity management system. We must consider what to do if a vulnerability arises or an incident occurs and how to manage it. The supply chain theme is relevant, not only for the automotive industry but also for other sectors. What if my supplier also has risks? How well is it protected? Up to the general management of vulnerabilities, which must be actively addressed, not passively. We need to implement awareness and training measures, deal with encryption issues, and think about how to manage access control and authentication. All these topics are already known. Orchestrating all this is the challenge. That is, how do I bring all these requirements together? How far should I go? What is reasonable and what is excessive? The bad news is that European law does not clearly communicate minimum requirements. Each country still has some flexibility to act accordingly. However, the law acts as a minimum harmonization standard. This means it can always get worse. A country can always step up; it can set demanding standards if suitable for the country. NIS2 considers itself as minimal harmonization.
Below is a summary of the main articles from the NIS-2 directive:
Article 21 Measures for the Management of Cybersecurity Risks
Security requirements for the network and information systems of entities must include at least the following:
- Policy on risk analysis and security of information systems;
- Incident handling;
- Business continuity, such as backup management and emergency plans, and crisis management;
- Security of the supply chain, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers;
- Security in acquiring, developing, and maintaining network and information systems, including vulnerability response and disclosure;
- Policies and procedures to assess the effectiveness of cybersecurity risk management measures;
- Basic practices in cyber hygiene and cybersecurity training;
- Policies and procedures regarding the use of cryptography and, if applicable, encryption;
- Security aspects related to personnel, access policies, and asset management;
- When appropriate, the use of multi-factor authentication or continuous authentication solutions, secure voice, video, and text communication, and secure emergency communication systems within the entity.
There are various ways to address all of this, and this law, of course, also imposes requirements, such as cyber hygiene and training. For instance, cyber hygiene involves locking your computer screen when leaving your workstation, ensuring only someone else with the password can log in. The principle of a tidy desk also falls under cyber hygiene, meaning if there’s no contract on the desk, no one can photograph or steal it.
Training is necessary for both executives and regular employees. Additionally, we have concepts and procedures for cryptography, where we need to consider how to encrypt things, whether to encrypt at all, and if so, what, how, for how long, with what, and when to remove all of this. We also need to think about personnel quality and facility management. Of course, multi-factor authentication must be present; this law explicitly mentions it. So, anyone not using multi-factor authentication for critical applications today will need to consider what to do, as it is considered the state of the art, and the state of the art is no longer just a username and password.
Article 23 Reporting Obligations
Key and essential entities must immediately inform their competent authority of any security breach that significantly impacts the provision of their services.
- Early warning within 24 hours of becoming aware of the significant security breach;
- Reporting on the harmful incident within 72 hours, including the initial assessment, severity, impact, any compromising indicators;
- Interim reports may be requested by the authority at any time;
- After one month (at the latest), a final report with a description, severity, impact, remedy, nature of the threat, causes, remediation, cross-border consequences;
- In case of ongoing security breach, progress reports.
- Note: Trust service providers cannot apply the 72-hour rule.
After thoroughly describing, checking, and updating all of this, including confirmation by an external auditor, the question arises: how do we report, and what are the steps in case of a serious security incident? Key and essential entities must issue an early warning within 24 hours of notification. This requires well-thought-out policies, including who makes the report, who writes and reviews the content, who approves it, management signatures, and who warns other companies if necessary. Failing to meet reporting obligations can lead to liability for failure to disclose important information. Within 72 hours, there is an initial assessment, followed by interim and progress reports, along with various legally prescribed measures to support NIS directive implementation. If you don’t practice and document this in advance, it becomes challenging to meet these reporting obligations. It requires preparation and clear procedures to respond quickly and adequately to security incidents according to the guidelines.
Article 32 Supervision and Enforcement Measures
- On-site inspections and external supervision measures (by trained professionals, also without notice);
- Security audits (regularly, targeted, by an independent entity or competent authority);
- Request for information (risk management, cybersecurity, results of security audits, including evidence);
- Official instructions to the institution for measures within a reasonable period;
- Enforcement of public disclosure of breaches;
- Appointment of a supervisor (period);
- The costs of the security audit are borne by the audited institution;
- Fines, revocation of permits, exemption of management;
- Natural persons may be held liable for violations of their obligations to ensure compliance with the directive.
Supervisory measures can be quite painful, ranging from security audits and official instructions to the appointment of a supervisor observing what you do and how you do it every day for a month. The costs are, of course, borne by the audited institution. It can also quickly lead to fines or even the exemption of management, where someone has to transfer leadership of an organization because they have clearly violated the law or failed to comply with it. What is interesting here is that, unlike previous cases where fines were imposed on the company, now natural persons can also be held liable. So, if the management says they find all this nonsense and don’t want to implement it, it can hit their personal wallet instead of the company.
NIS2: From Cybersecurity Management to Document Control
The NIS2 directive includes rules on risk analysis, chain management, cybersecurity incident management, personnel training, and management evaluation. Components of this include multifactor authentication, secure voice, video, and text communication, and a clean-desk policy for protection against photography. After a cyber incident, there is a reporting obligation within 24 hours. Enforcement can be through random inspections or reports, with fines and personal liability risks for management as sanctions.
All these rules can be documented with an Information Security Management System (ISMS). It’s possible to use ISO 27001 as a guide (see this NIS2 to ISO27001/27002 mapping). A typical ISMS has between 80 and 130 documents that need to be followed, defined, archived, and made available. This way, procedures can be documented and prepared for inspections or reporting a security breach within 24 hours of knowledge.
A robust ISMS can be implemented in our Document Control, Shareflex® Quality Documents application for SharePoint Online. Implementation and evidence are largely based on documents. Regulations, processes, instructions, checklists, and reports need to be created, maintained, and updated in a timely manner. They must be understandable and goal-oriented, available in one place for all relevant persons, with version control and approval procedures, and support for updates (mandatory for review and updating).
Many of these NIS2 and ISO standards require that you manage your “documented information,” have a controlled process for approval, review it regularly, and provide it to the relevant users in the organization. All this is covered by Shareflex Quality Documents. This is relevant for ISO 9001, ISO 13485, ISO 27001, ISO 50001, and NIS2, as NIS2 is very similar to ISO 27001.
For ISO 27001, the standard for information security management, it is crucial to have strict control over the versions of information security documentation to comply with the standard. Here are some key aspects:
Version Control:
1. ISO 27001 requires that documents such as policy documents, procedures, and guidelines are regularly reviewed and updated.
2. Strict control over versions means that every change in the document is clearly documented, including details such as who made the change, when it happened, and the nature of the change.
Compliance and Audits:
1. During audits for ISO 27001 certification, an auditor will want to see that the information security system complies with the requirements of the standard.
2. Having a controlled version control process demonstrates that the organization is actively working to maintain and improve its information security documentation.
Risk Management:
1. ISO 27001 strongly focuses on risk management in relation to information security. Good version control helps ensure that any changes in documentation are carefully reviewed to minimize potential risks.
Reliability and Integrity:
1. Information security requires documentation to be reliable and integral. Strict control over versions helps ensure that employees always have access to the most recent and accurate information.
In summary, strict control over versions of information security documentation is a crucial part of the continuous improvement process required for maintaining ISO 27001 certification. It ensures that the information security system is effectively managed and adapted to changing circumstances and risks.
In a certification process, it must be demonstrated to an auditor that the requirements are met. During an audit, events from the past are mainly examined. Therefore, records of previous versions are necessary because the auditor wants to know how the guideline looked then. Having Shareflex® Quality Documents greatly helps in this regard.
Concluding
While NIS-2 may require significant efforts, its implementation promises enhanced cybersecurity across the EU. The Dutch NIS2 legislation is expected in 2025; however, the precise details are not yet known. Will the Netherlands step up compared to European legislation?
The transition to NIS2 compliance carries substantial implications for most entities falling under the directive’s scope, often necessitating a transitional period of 1-3 years. Therefore, it is imperative to initiate the requisite measures well in advance. If you already have an ISO 27001/27002 certification, check this mapping to the NIS2 directive for a quick start.
If you don’t have an ISO certification, consider acquiring a set of basic documents for ISO 27001, at Online-iso or Advisera.
For ISO 27001 (and consequently for NIS2), strict control over the versions of information security documentation is essential to meet the standard. For this, Lialis provides Shareflex Quality Documents, fully meeting this need. Essentially, a Document Control System is a specialized form of a DMS, optimized for organizations requiring strict control and compliance with quality standards.
Shareflex Quality Documents
Gain complete control over critical documents for quality management. A professional Document Control application for ISO-compliant document management.
- Quick and clear access to relevant information from the portal.
- Easy to use thanks to a seamless SharePoint Online experience.
- Each individual document contains mandatory linked master data (record metadata).
- Document control workflow that complies with the standard.
- Monitoring of document validity period.
- Comprehensive notification options, such as read receipt.
- Audit trail for documents and records, history of workflows, tasks, and messages.
- Comprehensive search options and saving personal search criteria.
- Daily cumulative email notifications about everything of importance.
- 100% SharePoint Online software, quick to implement and easy to learn.
- Software installed via script in your own M365 environment.
- Reporting through Excel and/or Power BI.
- Full support for the security configuration of your M365 tenant.
- You manage the access rights yourself, so no hassle with yet another cloud vendor.
- Always online access to the system via a web browser, MS Teams, or Power App.
- Full integration with MS Office, including the transfer of master data.
- Legally compliant archiving of all (obsolete) data on secure long-term storage with Microsoft 365 features (Microsoft Purview).

Use the scroll wheel on your mouse to quickly explore our document control software on SharePoint Online.